Securing the HP BIOS with HP Sure Admin using HP CMSL – (Upd 9/10/2024 - added info on KMS available from Azure marketplace)
In order to provide a more secure access to the BIOS, HP introduced Sure Admin on commercial systems. HP Sure admin depends on a cryptographically secure infrastructure, the Secure Platform Management (SPM), previously released in the BIOS to support features such as HP Sure Run and Sure Recover. HP SPM uses public key cryptography where a private key signs a payload and the target system uses the associated public key to verify its legitimacy when downloaded. Enabling Sure Admin requires provisioning of a signed payload, and that Secure Platform Management be provisioned in the BIOS. HP Sure Admin is a significantly more secure method for communicating with the BIOS than passwords, which can be leaked, stolen, or misused.
Overall steps to send a secure payload to the BIOS (e.g. Feature enablement, BIOS update, BIOS setting change, etc.)
- Payload is developed
- Payload is signed
- Payload is sent to target device
- BIOS checks Payload for validity
- BIOS accepts Payload (or rejects, if not valid)
HP Sure Admin is a feature on most Pro/Elite/Z HP commercial systems manufactured since 2018 (for some systems an up-to-date BIOS will be required for the first generation - aka the G5 generation).
NOTE: In the BIOS, HP Sure Admin has a setting called ‘Enhanced BIOS Authentication Mode (EBAM) and Enhanced BIOS Authentication Mode Local Access Key1 (LAK). We will use HP Sure Admin and EBAM interchangeably in this guide.
Secure Platform Management provisioning is explained on a separate blog post. That blog reviews the use of public/private keys and certificates, and how to provision the certificates as payloads, using OpenSSL (for certificate creation) as example. It also shows the use of HP Client Management Script Library (CMSL) commands to provision the certificates on a target device.
This blog assumes that HP SPM has been provisioned and illustrates how to enable Sure Admin. We will also provide examples for doing BIOS firmware updates and changing BIOS settings securely without the need for BIOS passwords.
HP Sure Admin Getting Started Guide explains some of the concepts behind the technology.
Sample PowerShell scripts that demonstrate SPM and Sure Admin provisioning and enablement are hosted on a GitHub repository , and are freely available to learn and draw from. Currently, the repository holds several PowerShell scripts, Create_Certs.ps1, to create all needed certificates, Create_Payloads.ps1, to create provisioning payloads for enabling SPM and EBAM/LAK, and provision and deprovision scripts, Provision_SPM.ps1 and Provision_EBAM.ps1, for execution on client PCs. These scripts are sample scripts used to demonstrate how OpenSSL (in lieu of a company’s CA) and CMSL commands can be used to setup and provision both HP SPM and EBAM/LAK.
NOTE: For additional security of the Signing Key, a certificate password may be used. In that case, it will be required as an argument to sign all payloads.Securing the BIOS with certificates (with Sure Admin) also means that BIOS updates will require specific handling, including the signing of the new BIOS firmware capsule and using Sure Admin commands for the update. The same is also true for doing BIOS manintenance actions, like setting specific BIOS settings. This will require a signed payload that the now secured BIOS will accept as valid. Examples are shown below in this blog.
NOTE: in order to fully disable HP Sure Admin, the CMSL provides specific commands, but note that the Local Access Key must be removed as well or the user will continue to see a QR code when attempting to enter the BIOS locally after pressing F10 during boot.
Enabling HP Sure Admin
As already mentioned, HP SPM must be provisioned to allow the Sure Admin BIOS protection feature to be enabled. To confirm the provisioning state of a target device, we can use the Get-HPSecurePlatformState CMSL command:
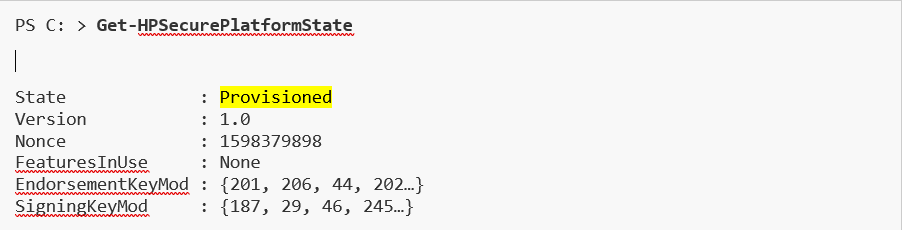
If the returned state is 'NotConfigured', then SPM must be provisioned first. If it shows ‘ProvisioningInProgress’, then a reboot is required (and PPI accepted) before Sure Admin can be enabled - meaning the SPM certificates (the Endorsement Key, at least) were loaded, and will require a reboot to take effect.
When the command returns a State of ‘Provisioned’, we can move on to Enable Sure Admin (EBAM/LAK)
To enable EBAM, we use the SPM’s Signing Key to create a secure certificate payload (NOTE: certificate names are not important):
PS C: > New-HPSureAdminEnablePayload -SigningKeyFile SK.Pfx -OutputFile SAEnablepayload.dat
As shown in the example above, to enable HP Sure Admin we create a payload which we sign with the private key of the signing key certificate, SK.pfx. When executing this payload on the client platform, the already provisioned public key of this signing key certificate is used to verify the authenticity and legitimacy of this payload. Only payloads which are signed with the corresponding private key are accepted.
NOTE: your private keys must never leave your secure environment. Do not distribute them to your clients, and do not depend on the PFX file password. The only part of your certificate that may leave your secure location is the public component of the certificate. The opaque payload created by the New-* functions contain only public information.
NOTE: a payload can only be used once on a specific device. This is due to the additional anti-replay protection developed in Sure Admin. A provisioned Payload will mark a nonce value that continually increases, and will prevent a used payload from being reused. You will have to reset the nonce counter in some situations.
In the future, a de-provisioning payload could be created to disable EBAM:
PS C: > New-HPSureAdminDisablePayload -SigningKeyFile SK.Pfx -OutputFile SADisablePayload.dat
NOTE: security of this process requires that commands not be able to be replayed – and potentially changing the security posture of the BIOS. There are Anti-Replay counters for both Secure Platform and Sure Admin/EBAM to prevent this from happening. Meaning, a payload that was created at some point in time contains a number (the Nonce) that is compared against the Anti-Replay counters in the BIOS, which increase in value as they are used. If the nonce counter in the payload is not higher, the payload will be rejected. For this reason, it might be useful to delay the creation of the Disable payload until ready to be used. The CMSL commands to create payloads have a -nonce argument that can be used for this purpose.
Creation of the EBAM and LAK payloads should be done on a secure system with access to the Signing Key. Provisioning requires the payload file and CMSL module (1.6 or later) to be available on the client. The following command, executed on the target PC, is used to provision the security payloads:
PS C: > Set-HPSecurePlatformPayload -PayloadFile SAEnablepayload.dat
Once this step is executed (no reboot required), modifying BIOS settings programmatically will require special handling.
These are some of the PowerShell cmdlets that support EBAM BIOS administration:
Get‐HPSureAdminState - Get the current state of the HP Sure Admin feature
New-HPSureAdminFirmwareUpdatePayload - Generate a payload for authorizing a firmware update
New-HPSureAdminBIOSSettingValuePayload - Generate a payload for authorizing a single BIOS setting change.
New-HPSureAdminBIOSSettingsListPayload - Generate a payload for authorizing multiple BIOS setting changes
New-HPSureAdminSettingDefaultsPayload - Generate a payload for resetting BIOS settings to default values
For details on any of these commands, PowerShell's Get-Help comes in handy.
PS C: > Get-Help New-HPSureAdminFirmwareUpdatePayload
Provisioning of LAK setting is the next step that is required to fully provision a PC for Sure Admin. This additional step ensures that BIOS settings are protected against modification by an unauthorized user with physical access to the F10 BIOS setup capability.
Enabling F10 BIOS Access with LAK
The Sure Admin 'Enhanced BIOS Authentication Mode Local Access Key1' (LAK), must be configured to fully protect a device in Sure Admin mode. After enabling EBAM with a payload, an LAK certificate payload must then be provisioned to secure the BIOS from unauthorized F10 access.
The scripts on the GitHub repository will create the certificate used by the Local Access Key, as well as the corresponding provisioning payload for loading on the target.
Once the Local Access Key is provisioned, the F10 BIOS Setup menu is secured with a certificate, which when accessed, it challenges the user on screen with a QR Code. The QR Code is generated from the Local Access Key public certificate loaded on the system. To proceed and enter the BIOS, a PIN is required.
The idea is that a user or IT staff, with a phone app called 'HP Sure Admin' (Android or iOS supported) can respond to the challenge by scanning the QR Code and then using the 6-digit PIN provided by the app to access the BIOS. In order to be able to derive the PIN, the app will have to have access to the LAK private key of the public/private pair created previously. we'll discuss how this can be done later.
Setting up Local Access Key
First, we create the certificate to enable Local Access Key using the same technique we used for creating SPM certificates. This was described in the blog for working with SPM. In our case we are doing something similar but creating a PKCS#12 .pfx certificate for LAK, also signed by SPM’s Signing key (the same that was used to provision SPM on a client PC).
We then create a signed payload to provision LAK on the device, with a HP CMSL command (again, version 1.6 or newer required), like this:
# ----- Create the LAK certificate (Use Signing Key) $CertSubj = '/C=US/ST=State/L=City/O=Company/OU=Org/CN=SPMdemo' PS C: > openssl.exe req -x509 ` -nodes -newkey rsa:2048 -keyout LAKpriv.pem -out LAKcert.crt -days 3650 ` -subj $CertSubj 2>$null PS C: > openssl.exe pkcs12 -inkey LAKpriv.pem -in LAKcert.crt -export ` -keypbe PBE-SHA1-3DES -certpbe PBE-SHA1-3DES -out LAK.Pfx ` -name 'EBAM Local Access Key Certificate' -passout pass:“P@ssw0rd” 2>$null # ----- Create LAK enable payload from certificate (for scenario where LAK private key is stored in Key Management Service- KMS ) PS C: > New-HPSureAdminLocalAccessKeyProvisioningPayload -SigningKey SK.pfx ` -LocalAccessKeyFile LAK.pfx -OutputFile LAKPayload.DAT ` -KeyEnrollmentData "2?{'V':'2','KMS':{'URL':'https://myKMS.azurewebsites.net/api'}}" # ----- Create LAK enable payload from certificate (for scenario where LAK private key is stored on the phone) PS C: > New-HPSureAdminLocalAccessKeyProvisioningPayload -SigningKeyFile SK.Pfx ` -LocalAccessKeyFile LAK.Pfx -OutputFile LAKpayload.dat # ----- Provision LAK on the client PS C: > Set-HPSecurePlatformPayload -PayloadFile LAKPayload.dat
Remember that the signing key file (AND its password, if used) MUST match what was used previously, or the payload will be rejected.
In the future, a deprovisioning payload can be created (to remove the certificate):
PS C: > New-HPSureAdminBIOSSettingValuePayload -SigningKeyFile SK.Pfx -Name "Enhanced BIOS Authentication Mode Local Access Key 1" -Value "" -OutputFile LAKDepropayload.dat # ----- De-Provision LAK on the client PS C: > Set-HPSecurePlatformPayload -PayloadFile LAKDepropayload.dat
How Local Access Key works
Once the LAK certificate is provisioned , when the user hits F10 at power on there will be a challenge with a QR Code and a PIN entry field:

The user then opens the ‘HP Sure Admin’ app on the phone, clicks on ‘Scan QR Code’ button, points to the screen to scan the code, and shortly the app will display the required PIN

Now the question is, how does the phone app know to respond to the QR Code challenge and provide an appropriate PIN? The answer is that the ‘HP Sure Admin’ app has access to the LAK Private key.
Access to the LAK Private Key to Unlock F10 BIOS Access
There are a couple of ways the phone app can resolve the PIN challenge from the BIOS’s LAK certificate.
- The most secure method to access the LAK Private key is by setting up a remote Key Management Service (KMS). The ‘HP Sure Admin’ phone app, via information scanned from the QR Code, is designed to contact an Azure Domain tenant preconfigured with a Sure Admin module. The app provides the KMS with the challenge data, and in return receive the appropriate LAK PIN to type in the BIOS screen. The KMS, with access to the LAK private key, can resolve and respond with the PIN.
HP Softpaq sp143492 contains the software modules required to set up an Azure KMS service provider. When configured, the Local Access KMS in Azure exposes web APIs used by the HP Sure Admin Local Access Authenticator phone application to obtain one-time-access PINs for authorized users without exposing the private Local Access Key. An additional resource for help implementing the Sure Admin KMS from the Azure marketplace, you can reach out to hpsureadmin-info@hp.com.
To upload a local access key into the Azure KMS, HP Client Management Script Library (HP CMSL) provides a PowerShell cmdlet, designed for this purpose and easy to use.
PS C: > New-HPSureAdminLocalAccessKeyProvisioningPayload -SigningKey SK.pfx ` -LocalAccessKeyFile LAK.pfx -OutputFile LAKPayload.DAT ` -KeyEnrollmentData "2?{'V':'2','KMS':{'URL':'https://myKMS.azurewebsites.net/api'}}" # ----- Set the Local Access Payload on device PS C: > Set-HPSecurePlatformPayload -PayloadFile LAKPayload.dat # ----- and upload LAK Private Key to KMS PS C: > Send-HPSureAdminLocalAccessKeyToKMS -LocalAccessKeyFile LAK.pfx
NOTE: the CMSL command above to send the private keys to the Azure KMS is available with release 1.6.2. The Send-HPSureAdminLocalAccessKeyToKMS command can take additional options to properly configure the action to be taken when the KMS module receives the local access request. Details at https://developers.hp.com/hp-client-management/doc/Send%E2%80%90HPSureAdminLocalAccessKeyToKMS
- Alternatively, we can provision LAK Private Key directly on the HP Sure Admin phone app. This is done by scanning the QR Code generated from that key, same as scanning the challenge QR Code on the screen. In order to generate the QR Code of the LAK private key, there is an CMSL command that will do just that, e.g. create a jpg from the key file:
PS C: > Convert-HPSureAdminCertToQRCode -LocalAccessKeyFile LAK.pfx -OutputFile LAK_QRCode.jpg -Passphrase ”P@ssw0rd” # -ViewAs Image (Default)
This command extracts a private key from the provided certificate file and presents it in a form of QR-Code. Once scanned, the app can be used for authorizing command and BIOS setting changes. Obviously, care must be taken to ensure the scanned code information in the phone remains secure, since it contains the LAK private key data.
Using HP Sure Admin examples
Modify a single BIOS setting value
The New-HPSureAdminBIOSSettingValuePayload can be used to create a payload to deploy to one or many systems. We create the value setting and then apply it with the Set-HPSecurePlatformPayload cmdlet:
# ----- Create a BIOS setting value change payload
PS C: > New-HPSureAdminBIOSSettingValuePayload -Name ”Fast Charge” -Value Enable -SigningKeyFile SK.pfx -OutputFile payload.dat
# ----- Deliver the BIOS setting change payload
PS C: > Set-HPSecurePlatformPayload -PayloadFile payload.dat
Note the use of the SPM Signing Key private key (SK.pfx) to create the payload. If the payload file is not signed with the Signing Key used to provision SPM, then it will be rejected by the BIOS. Also, remember to use the Signing Key password, if needed
Modifying multiple settings
In order to change several settings at once, we require a file with the right content. The file can be formatted as xml, json, bcu, or csv. Let’s use the BCU file type as this is also how the BiosConfigUtility modifies settings and is commonly used today. Let’s start with this file, which will be named BCUDemo.txt
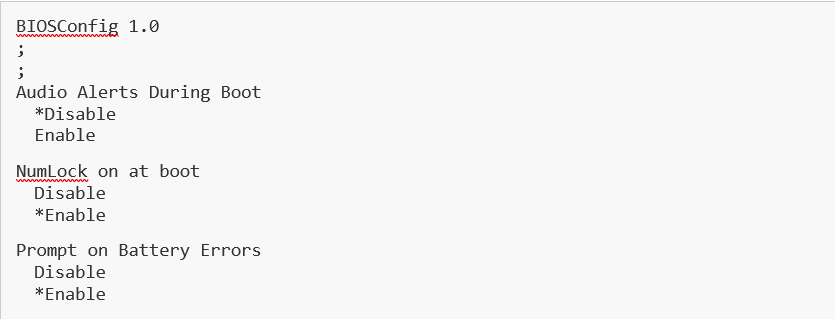
Next, we create the payload, and use the payload to provision the device as before.
# ----- Create a BIOS multiple settings changes payload PS C: > New-HPSureAdminBIOSSettingsListPayload -InputFile ”BCUdemo.txt” -Format BCU -SigningKeyFile SK.pfx -OutputFile BIOSpayload.dat # ----- Deliver the BIOS setting change payload PS C: > Set-HPSecurePlatformPayload -PayloadFile BIOSpayload.dat
Updating the BIOS
To update a BIOS, the firmware must first be retrieved, a BIOS provision payload created, and then the BIOS update done, all with HP CMSL commands
Let’s try an example for an Elitebook 840 G6 notebook – Platform ID/SysID = 8549. On a hosting server, download the BIOS bin file and create the f/w signed payload - we can use the CMSL Get-HPBIOSUpdates command:
PS C: > Get-HPBIOSUpdates -Platform 8549 -Download # download latest version
As of this writing, the latest BIOS for the platform is R70_010702.bin.
NOTE: We then create a firmware update payload showing that the Signing Key that was provisioned was created with a password. If the key was created without a password, do not use the -SigningKeyPassword argument, or the payload will fail on the client.
# ----- Create the BIOS f/w update payload: will include the appropriate key and be associated withe the bios bin file
PS C: > New-HPSureAdminFirmwareUpdatePayload -File R70_010702.bin -SigningKeyFile SK.pfx -OutputFile FWpayload.dat
To deploy the new BIOS, copy the bin and dat payload files to the client PC, and execute the update command. Also, manage Bitlocker option if needed
# ----- execute on client PC
PS C: > Update-HPFirmware -File R70_010702.bin -PayloadFile FWpayload.dat -Quiet -Bitlocker Suspend # other options: Ignore|stop
You can run a command to confirm the current BIOS version on the platform. Note that the BIOS will not flash firmware not compatible with it.
PS C: > Get-HPBIOSUpdates -Check # returns $true if BIOS is up to date





